Good link for job interview preperations https://github.com/yash0530/InterviewPrepResources
Thursday, December 24, 2020
Tuesday, December 15, 2020
Saturday, December 12, 2020
Sunday, December 6, 2020
Saturday, December 5, 2020
What's a priority queue?
'Ladies first' is an instance of 'min priority queue', where as a queue free from any such bias is a normal queue.
Difference between creating a heap and heapify
Creating a Heap is inserting all the elements of a given array into an existing heap assuming the first element of the given array as the initial heap, where as Heapify is simply creating a CBT ( complete binary tree) with all the elements of the given array and then converting that CBT into a heap, by moving up from the last non-leaf node up to the root.
Why time complexity of Heapify is O(n)?
Look at this first then you may Have a look here also.
Harmonic progression this is needed to understand the above.
Monday, November 23, 2020
Sunday, November 22, 2020
Wednesday, November 4, 2020
Structured programming Vs object-oriented programming
There is no formal definition of structured programming, but most agree that it must have a top-down design and use only the three types of logical structures :
1. Sequence (top-down): Statements are executed one after the other.
2. Decisoins (if-else): One of the several blocks of the program is executed based on a test or condition.
3. Iterations (loops ): One or more statements are executed repeatedly as long as a specified condition is met.
Object-Oriented programming:
Can be viewed as a collection of cooperating objects. We use a blend of traditional structured programming along with OOPs.
An object is an encapsulation of data and code that operates on that data. It is the most effective style of programming for solving complex problems and implementing complex systems in computer softwares.
Tuesday, November 3, 2020
Tuesday, October 27, 2020
Drawing a circle using OpenGL
// C program to demonstrate
// drawing a circle using
// OpenGL
#include<stdio.h>
#include<GL/glut.h>
#include<math.h>
#define pi 3.142857
// function to initialize
void myInit (void)
{
// making background color black as first
// 3 arguments all are 0.0
glClearColor(0.0, 0.0, 0.0, 1.0);
// making picture color green (in RGB mode), as middle argument is 1.0
glColor3f(0.0, 1.0, 0.0);
// breadth of picture boundary is 1 pixel
glPointSize(2.0);
glMatrixMode(GL_PROJECTION);
glLoadIdentity();
// setting window dimension in X- and Y- direction
gluOrtho2D(-780, 780, -420, 420);
}
void display (void)
{
glClear(GL_COLOR_BUFFER_BIT);
glBegin(GL_POINTS);
float x, y, i;
// iterate y up to 2*pi, i.e., 360 degree
// with small increment in angle as
// glVertex2i just draws a point on specified co-ordinate
for ( i = 0; i < (2 * pi); i += 0.001)
{
// let 200 is radius of circle and as,
// circle is defined as x=r*cos(i) and y=r*sin(i)
x = 200 * cos(i);
y = 200 * sin(i);
glVertex2i(x, y);
}
glEnd();
glFlush();
}
int main (int argc, char** argv)
{
glutInit(&argc, argv);
glutInitDisplayMode(GLUT_SINGLE | GLUT_RGB);
// giving window size in X- and Y- direction
glutInitWindowSize(1366, 768);
glutInitWindowPosition(0, 0);
// Giving name to window
glutCreateWindow("Circle Drawing");
myInit();
glutDisplayFunc(display);
glutMainLoop();
}
Output:
Scanline Polygon Fill Algorithm
#include<GL/glut.h>
#include<stdio.h>
float x1,x2,x3,x4,y1,y2,y3,y4;
void draw_pixel(int x,int y)
{
glColor3f(0.0,1.0,1.0);
glPointSize(1.0);
glBegin(GL_POINTS);
glVertex2i(x,y);
glEnd();
}
void edgedetect(float x1,float y1,float x2,float y2,int *le,int *re)
{
float temp,x,mx;
int i;
if(y1>y2)
{
temp=x1,x1=x2,x2=temp;
temp=y1,y1=y2,y2=temp;
}
if(y1==y2)
mx=x2-x1;
else
mx=(x2-x1)/(y2-y1);
x=x1;
for(i=y1;i<=y2;i++)
{
if(x<(float)le[i]) le[i]=(int)x;
if(x>(float)re[i]) re[i]=(int)x;
x+=mx;
}
}
void scanfill(float x1,float y1,float x2,float y2,float x3,float y3,float x4,float y4)
{
int le[500],re[500],i,j;
for(i=0;i<500;i++)
le[i]=500,re[i]=0;
edgedetect(x1,y1,x2,y2,le,re);
edgedetect(x2,y2,x3,y3,le,re);
edgedetect(x3,y3,x4,y4,le,re);
edgedetect(x4,y4,x1,y1,le,re);
for(j=0;j<500;j++)
{
if(le[j]<=re[j])
for(i=le[j];i<re[j];i++)
draw_pixel(i,j);
}
}
void display()
{
//x1=250.0;y1=200.0;x2=150.0;y2=300.0;x3=250.0;
//y3=400.0;x4=350.0;y4=300.0;
x1=50.0;y1=300.0;x2=300.0;y2=250.0;x3=250.0;
y3=70.0;x4=70.0;y4=90.0;
glClear(GL_COLOR_BUFFER_BIT);
glColor3f(0.0,0.0,1.0);
glBegin(GL_LINE_LOOP);
glVertex2f(x1,y1);
glVertex2f(x2,y2);
glVertex2f(x3,y3);
glVertex2f(x4,y4);
glEnd();
scanfill(x1,y1,x2,y2,x3,y3,x4,y4);
glFlush();
}
void init()
{
glClearColor(1.0,1.0,1.0,1.0);
glMatrixMode(GL_PROJECTION);
glLoadIdentity();
gluOrtho2D(0.0,499.0,0.0,499.0);
}
int main(int argc,char **argv)
{
glutInit(&argc,argv);
glutInitDisplayMode(GLUT_SINGLE|GLUT_RGB);
glutInitWindowSize(500,500);
glutCreateWindow("Scanline polgon fill algorithm");
glutDisplayFunc(display);
init();
glutMainLoop();
return 0;
}
Output:
Drawing a Wireframe using OpenGL
// C program to demonstrate
// drawing a hard wire house
// OpenGL
#include<stdio.h>
#include<GL/glut.h>
#include<math.h>
#define pi 3.142857
// function to initialize
void myInit (void)
{
// making background color grey as first
// 3 arguments all are 0.4
glClearColor(0.4, 0.4, 0.4, 0.4);
// making picture color green (in RGB mode), as middle argument is 1.0
glColor3f(0.0, 1.0, 0.0);
// breadth of picture boundary is 2 pixel
glPointSize(2.0);
glMatrixMode(GL_PROJECTION);
glLoadIdentity();
// setting window dimension in X- and Y- direction
gluOrtho2D(0.0,200.0, 0.0,150.0);
}
void display (void)
{
glClear(GL_COLOR_BUFFER_BIT);
glBegin(GL_LINES);
//horizontal base of the house
glVertex2i(50,0);
glVertex2i(100,0);
//horizontal ceiling of the house
glVertex2i(50,50);
glVertex2i(100,50);
//left roof top
glVertex2i(50,50);
glVertex2i(75,100);
//right roof
glVertex2i(75,100);
glVertex2i(100,50);
//left wall
glVertex2i(50,0);
glVertex2i(50,50);
//right wall
glVertex2i(100,0);
glVertex2i(100,50);
//Door top
glVertex2i(65,40);
glVertex2i(85,40);
//Door left side
glVertex2i(65,40);
glVertex2i(65,0);
//Door right side
glVertex2i(85,40);
glVertex2i(85,0);
//Roof Box top
glVertex2i(65,65);
glVertex2i(85,65);
//Roof Box bottom
glVertex2i(65,55);
glVertex2i(85,55);
//Roof Box left side
glVertex2i(65,65);
glVertex2i(65,55);
//Roof Box right side
glVertex2i(85,65);
glVertex2i(85,55);
//Out Box bottom left
glVertex2i(0,25);
glVertex2i(25,0);
//Out Box bottom right
glVertex2i(50,25);
glVertex2i(25,0);
//Out Box top left
glVertex2i(25,50);
glVertex2i(0,25);
//Out Box top right
glVertex2i(25,50);
glVertex2i(50,25);
glEnd();
glFlush();
}
int main(int argc, char** argv)
{
glutInit(&argc, argv);
glutInitDisplayMode(GLUT_SINGLE | GLUT_RGB);
// giving window size in X- and Y- direction
glutInitWindowSize(800,600);
glutInitWindowPosition(0,0);
// Giving name to window
glutCreateWindow("Drawing a Hard wire House");
myInit();
glutDisplayFunc(display);
glutMainLoop();
}
Output:
Draw a circle inside a triangle using OpenGJ
// C program to demonstrate
// drawing a circle using
// OpenGL
#include<stdio.h>
#include<GL/glut.h>
#include<math.h>
#define pi 3.142857
// function to initialize
void myInit (void)
{
// making background color black as first
// 3 arguments all are 0.4
glClearColor(0.4, 0.4, 0.4, 1.0);
// making picture color green (in RGB mode), as middle argument is 1.0
//glColor3f(0.0, 1.0, 0.0);
// breadth of picture boundary is 1 pixel
glPointSize(1.0);
glMatrixMode(GL_PROJECTION);
glLoadIdentity();
// setting window dimension in X- and Y- direction
gluOrtho2D(0.0,800.0, 0.0,600.0);
}
void display (void)
{
glClear(GL_COLOR_BUFFER_BIT);
glBegin(GL_LINES);
//set color to draw the triangle
glColor3f(1.0,0.5,0.0);
//first horizontal side of the triangle
glVertex2i(100,50);
glVertex2i(700,50);
//left side of the triangle
glVertex2i(100,50);
glVertex2i(400,500);
//third vertex
glVertex2i(400,500);
glVertex2i(700,50);
glEnd();
glBegin(GL_POINTS);
glColor3f(0.0, 1.0, 0.0);
float x, y, i;
// iterate y up to 2*pi, i.e., 360 degree
// with small increment in angle as
// glVertex2i just draws a point on specified co-ordinate
for ( i = 0; i < (2 * pi); i += 0.001)
{
// let 200 is radius of circle and as,
// circle is defined as x=r*cos(i) and y=r*sin(i)
x = 400+ 100 * cos(i);
y = 200+ 100 * sin(i);
glVertex2i(x, y);
}
glEnd();
glFlush();
}
int main(int argc, char** argv)
{
glutInit(&argc, argv);
glutInitDisplayMode(GLUT_SINGLE | GLUT_RGB);
// giving window size in X- and Y- direction
glutInitWindowSize(800,600);
glutInitWindowPosition(0, 0);
// Giving name to window
glutCreateWindow("Drawing Green Circle inside Orange Triangle");
myInit();
glutDisplayFunc(display);
glutMainLoop();
}
Output:
Cohen Line clipping algorithm
// C++ program to implement Cohen Sutherland algorithm
// for line clipping.
#include <iostream>
#include <GL/glut.h>
using namespace std;
// Defining region codes
const int INSIDE = 0; // 0000
const int LEFT = 1; // 0001
const int RIGHT = 2; // 0010
const int BOTTOM = 4; // 0100
const int TOP = 8; // 1000
// Defining x_max, y_max and x_min, y_min for
// clipping rectangle. Since diagonal points are
// enough to define a rectangle
const int x_max = 100;
const int y_max = 100;
const int x_min = 40;
const int y_min = 40;
int x1,x2,y1,y2;
// Function to compute region code for a point(x, y)
int computeCode(double x, double y)
{
// initialized as being inside
int code = INSIDE;
if (x < x_min) // to the left of rectangle
code |= LEFT;
else if (x > x_max) // to the right of rectangle
code |= RIGHT;
if (y < y_min) // below the rectangle
code |= BOTTOM;
else if (y > y_max) // above the rectangle
code |= TOP;
return code;
}
// Implementing Cohen-Sutherland algorithm
// Clipping a line from P1 = (x2, y2) to P2 = (x2, y2)
void cohenSutherlandClip(double x1, double y1,double x2, double y2)
{
// Compute region codes for P1, P2
int code1 = computeCode(x1, y1);
int code2 = computeCode(x2, y2);
// Initialize line as outside the rectangular window
bool accept = false;
while (true)
{
if ((code1 == 0) && (code2 == 0))
{
// If both endpoints lie within rectangle
accept = true;
break;
}
else if (code1 & code2)
{
// If both endpoints are outside rectangle,
// in same region
break;
}
}
if (accept)
{
cout <<"Line accepted from (" << x1 << ", "
<< y1 << " to "<< x2 << ", " << y2 << ") because its completely VISIBLE" << endl;
// Here the user can add code to display the rectangle
// along with the accepted (portion of) lines
}
else
cout <<"Line rejected from (" << x1 << ", "
<< y1 << " to "<< x2 << ", " << y2 << ") because its completely INVISIBLE" << endl;
}
void display()
{
glClear(GL_COLOR_BUFFER_BIT);
glColor3f(0.0,1.0,0.0);
glBegin(GL_LINES);
glVertex2i(40,100);
glVertex2i(40,10);
glVertex2i(100,100);
glVertex2i(100,10);
glVertex2i(40,100);
glVertex2i(100,100);
glVertex2i(40,10);
glVertex2i(100,10);
glColor3f(1.0,0.0,0.0);
//Visible line
glVertex2i(50,60);
glVertex2i(70,40);
//Invisible line
glVertex2i(150,100);
glVertex2i(180,50);
glEnd();
glFlush();
}
void myInit(void)
{
glClearColor(0.0,0.0,0.0,1.0);
glPointSize(2.0);
glMatrixMode(GL_PROJECTION);
glLoadIdentity();
gluOrtho2D(0,200,0,200);
}
// Driver code
int main(int argc, char**argv)
{
cout<<" The coordinates of the clipping window are (40,100), (100,100), (100,10) and (40,40)"<<endl;
// First Line segment
// P11 = (5, 5), P12 = (7, 7) completely VISIBLE(inside)
cohenSutherlandClip(50, 60, 70, 40);
// P11 = (5, 5), P12 = (7, 7) completely INVISIBLE(outside)
cohenSutherlandClip(150, 100, 180, 150);
glutInit(&argc, argv);
glutInitDisplayMode(GLUT_SINGLE | GLUT_RGB);
// giving window size in X- and Y- direction
glutInitWindowSize(400,400);
glutInitWindowPosition(0,0);
// Giving name to window
glutCreateWindow("Cohen-Sutherland line clipping algorithm");
myInit();
glutDisplayFunc(display);
glutMainLoop();
return 0;
}
output:
Thursday, October 8, 2020
Python String methods
- title()
- capitalize()
- swapcase()
- find()
- count()
- replace()
- isalnum()
- format()
- reverse()
- clear()
- add
- append()
- update()
Monday, October 5, 2020
MCA subject Video classes
- MCS 31 (Design and Analysis of Algorithms)
- Introduction to Data Structures & Algorithms - IIT Delhi
- Introduction to Data Structures & Algorithms
- Sorting Algorithms & Asymptotic Analysis II - IGNOU
- Algorithmic Techniques for problem solving 2
- Stack Applications
- Queue Data Structure
- An introduction to trees
- DAA - Abdul Bari
- DAA - Javatpoint
- Merge sort, how multiple recursion works under the hood - Jenny's Lectures
- Shell sort - Jenny's Lectures
- Bubble sort - Jenny's Lectures
- TutorialsPoints - Analysis of Algorithms
- Average case analysis - Abdul Bari
- Amortized analysis of Algorithms
- Best First Search algorithm an example.
- Topological Sort or Ordering of a Graph - Jenny's Lectures
- Probabilistic (randomized) Algorithms
- Genetic Algorithms - Nature inspired Algorithms IIT KGH
- TC - IITKGP
- PDA Introduction - Neso Academy.
- Theory of Computation - Neso Academy
- Compiler Design IIT KGP
- MCS 33 (Advanced Discrete Mathematics - Recurrence Relations & Graph Theory
- MCS 34 (Software Engineerig)
- Software Engineering - IIT KGP
- Fact Finding Techniques 1
- Software Engineering Process An Overview - IGNOU
- Advanced Software Engineering Projects - IGNOU
- Spiral Life Cycles Models
- Life cycle models 2 Win Win Spiral Model - IGNOU
- MCS 42 (Computer Networks & Distributed Systems)
- MCS 43 (Advanced Database Management Systems)
- Advanced DBMS - limits of RDBMS
- Introduction to database systems IIT Madras
- Introduction to Relational Model/2 DBMS IIT Khg - Relational Algebra & its operations.
- MCS 51 (Advanced Java & Internet)
- Websites -1 - IGNOU
- Websites - 2 - IGNOU
- Servlets Basics - IGNOU
- Writing Servlets - IGNOU
- Session Tracking in Servlet programming - IGNOU
- Website management 1
- Website management 2
- Network Technology & Devices
- Basics of Internet
- Introduction to Computer & Networking
- Introduction to distributed systems - IGNOU
- Java Security
- MCS 52 (Management Information System)
- MCS 53 (Computer Graphics)
- IIT - Guwahati
- Computer Graphics - Projections
- Computer Graphics - Transformation - IGNOU
- Multimedia Tutorials
- MCSE 003 (Artificial Intelligence)
- Fundamentals of AI - IIT Guwahati
- Introduction to Artificial Intelligence 2
- Knowledge Representation Part 1
- Symbolic Logic Knowledge Representation - IGNOU
- Fuzzy Logic why and what 1 - IGNOU
- Fuzzy Logic why and what 2 - IGNOU
- AI programming languages 1 Part 1 LISP 4- IGNOU
- AI languages LISP Artificial Intelligence
- AI programming languages 1 Part 2 - IGNOU
- AI programming LISP 1
- LISP part - 3 Artificial Intelligence 1 - IGNOU
- LISP Part - 3 Artificial Intelligence 2 - IGNOU
- LISP Part 5 - IGNOU
- Uncertain Knowledge & Reasoning 1
- Uncertain Knowledge & Reasoning 2
- AI programming language LISP 3 - IGNOU
- AI programming language LISP - 4 - IGNOU
- Introduction to PROLOG
- A Start informed search algorithm
- AO Star informed search algorithm also called as the AND-OR graphs.
- AI Education 4u series.
- MCSE 004 (Numerical & Statistical Computing)
- Scientific Computing using MATLAB - IIT Delhi
- Numerical & Statistical Techniques - IGNOU
- Numerical & Statistical Computing 2
- Random Variables and Probability 3
- Normal Distribution
- Random variables & Probability distributions 4
- Numerical and Statistical Techniques 6
- MCSE 011 ( Parallel Computing a.k.a. Super Computing)
Sunday, October 4, 2020
Friday, October 2, 2020
Thursday, October 1, 2020
Retaining the color code in Notepad++
When you open a supported file format in Notepad++, it performs syntax highlighting where it formats the text with various colors to make reading easier.
However, when you save the file or copy text from it to an external program, all of the syntax highlighting and formatting is lost, and the text will take on formatting of the program you’re pasting into. This shouldn’t be surprising as the program is basically a plain-text editor. The syntax highlighting you see is just a visual enhancement. Although, there is a way to retain this formatting, i.e. if you have NppExport plugin installed. Latest builds of Notepad++ ships with this plugin. If you don’t have NppExport installed, you can download it through the inbuilt plugin manager.
When you have it ready, highlight the code that you want to copy, then go to
Plugins (on the menu bar) > Select NppExport > Copy all formats to clipboard
Now when you paste the code into a program that supports rich text formatting, for example Microsoft Word or Evernote, all of the formatting should be retained.
Tuesday, September 29, 2020
Competitive Programming
In CP there are two types of topics - general techniques (like DP, greedy, brute force) and particular algorithms (like graph, math, data structures).
Monday, September 28, 2020
Sunday, September 27, 2020
List of best online resources for software engineers
- https://www.tutorialride.com/
- https://cses.fi/problemset/
- https://www.java67.com/
- https://erdplus.com/
- https://www.youtube.com/watch?v=zWg7U0OEAoE&list=PLBF3763AF2E1C572F
- https://www.youtube.com/watch?v=qH6yxkw0u78&list=PL-pUjcDnciX3Z5AEE8HHRrcfj-987Ia94
- https://www.kaggle.com/learn/overview
- https://www.freecodecamp.org/news/new-online-courses/
- https://www.youtube.com/watch?v=n2D1o-aM-2s&list=PLh94XVT4dq02frQRRZBHzvj2hwuhzSByN
- https://www.tutorialspoint.com/cakephp/index.htm
- EJB coding
- coursera.org/learn/django-build-web-apps
- https://www.netacad.com/
- developers.turing.com/welcome
Friday, September 25, 2020
Default Route in a Routing device
Understanding the default route:
A default route is the route that takes effect when no other route is available for an IP destination address.
If a packet is received on a routing device, the device first checks to see if the IP destination address is on one of the device’s local subnets. If the destination address is not local, the device checks its routing table. If the remote destination subnet is not listed in the routing table, the packet is forwarded to the next hop toward the destination using the default route. The default route generally has a next-hop address of another routing device, which performs the same process. The process repeats until a packet is delivered to the destination.
The route evaluation process in each router uses the longest prefix match method to obtain the most specific route. The network with the longest subnet mask that matches the destination IP address is the next-hop network gateway.
The default route in IPv4 is designated as 0.0.0.0/0 or simply 0/0. Similarly, in IPv6, the default route is specified as ::/0. The subnet mask /0 specifies all networks, and is the shortest match possible. A route lookup that does not match any other route uses this route if it is configured and active in the routing table. To be active, the configured next-hop address must be reachable.
Administrators generally point the default route toward the routing device that has a connection to a network service provider. Therefore, packets with destinations outside the organization's local area network, typically destinations on the Internet or a wide area network, are forwarded to the routing device with the connection to that provider. The device to which the default route points is often called the default gateway.
Sources:
https://www.juniper.net/documentation/en_US/junos/topics/concept/default-route-understanding.html
Wednesday, September 23, 2020
Wednesday, September 16, 2020
Monday, September 14, 2020
Genesis of the word 'CAPCHA'
CAPCHA - "Completely Automatic Public turing test to tell Computers and Humans Apart".
You can also think of it as
CAPCHA = CAPTURE + GOTCHA
'gotcha' means - I have got you (used to express satisfaction at having captured or defeated someone or uncovered their faults).
This word was coined by Manuel Blum (born 1938) is a professor of computer science at Carnegie Mellon University, Pittsburgh, Pennsylvania.
Sunday, September 13, 2020
Saturday, September 12, 2020
What is a 'Internet Covert Channel'?
A covert channel is an evasion or attack technique that is used to transfer information in a secretive, unauthorized or illicit manner. A covert channel can be used to extract information from or implant information into an organization. An Internet covert channel is the digital equivalent of a briefcase with a secret compartment that a spy might use to slip sensitive documents past security guards into or out of a secure facility. An attacker can use Internet covert channels to transmit sensitive documents unobserved – in this case, bypassing network security measures rather than bypassing security guards. And just as a spy can use that same secret compartment to conceal a weapon from security guards when entering a secure facility, an attacker can use an Internet covert channels to conceal a cyberweapon, for example, a download of malware from an external server onto a host within an organization’s private network.
Internet covert channels can use conventional Internet protocols in unconventional ways. The channel endpoints – an infected computer and the attacker’s command and control computer – must use this evasion or attack software that recognizes and processes these unconventional techniques. Either a user or malware can install this software, or an attacker can install the software using a remote administration tool (RAT). Internet covert channels are different from encrypted tunnels. They can and do transfer information in plain text, but they’re unobserved. While they do not require encryption methods or keys, certain covert channels employ encryption or other means to obfuscate data.
source https://www.icann.org/news/blog/what-is-an-internet-covert-channel
In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy.
A covert channel is so called because it is hidden from the access control mechanisms of secure operating systems since it does not use the legitimate data transfer mechanisms of the computer system (typically, read and write), and therefore cannot be detected or controlled by the security mechanisms that underlie secure operating systems.
Covert channels are exceedingly hard to install in real systems, and can often be detected by monitoring system performance.
Covert channels can tunnel through secure operating systems and require special measures to control. Covert channel analysis is the only proven way to control covert channels.
There are two kinds of covert channels:
- Storage channels - Communicate by modifying a "storage location", such as a hard drive.
- Timing channels - Perform operations that affect the "real response time observed" by the receiver.
Storage Channels — Storage Covert channels encode covert data in the packets themselves (encoded in headers as I mentioned before). Timing (temporal) Channels —Delay between the packets is used to transmit data.
Link to Excellent explanation of covert-channels
Covert Channels are not efficient in terms of throughput. But they are quite good at hiding their presence, hence providing security by obscurity. If a covert channel is detected, it’s very likely to be entirely compromised unless the content is further protected by encryption.
A network protocol is basically a contract between a sender and a receiver, where the sender sends structured information in a format that can be interpreted by the receiver. This ‘structure’ of the information is defined as the ‘network packet’ structure. A packet mainly consists of 3 parts which are called the header, data, and an optional trailer. Firewalls and Intrusion Detection Systems (IDS) are particularly interested in the data section of a packet as it carries the actual payload of the transmission.
Video links on Covert channels
Thursday, September 10, 2020
Thursday, August 27, 2020
Tuesday, August 25, 2020
Monday, August 24, 2020
Sunday, August 23, 2020
Features of an Enterprise Application
What's an enterprise application means and what are its characterstics
How are enterprise built and what are its basic components
Thursday, August 20, 2020
Recursive problems: Example solutions
Problem 1:
'n' number of people are standing in a queue. People standing on even positions are selected. Of the selected people a queue is formed and again out of these only people on even position are selected. This continues until we are left with one person. Find out the position of that person in the original queue.
Solution:
#Python code
#declare a Global variable to store the last base case value of the recursion in it.
h = []
# The recursive function definition
def rec(l):
global h
m = []
#see the list after each recursive call
print(l)
#see the size of the new list after each recursive call
print(len(l))
#base case
if len(l) == 1:
h = l
if len(l)>1:
#Getting the even indexed elements of the list
for i in range(0,len(l)):
if (i+1) %2 == 0:
m = m + [l [i]]
# The above three lines can be replaced by following single line
# m = l[1::2] , this puts all the even indexed elements of list l in m. This also significantly improve #performance. Similarly, we can get odd indexed element with m = l[::2]
rec(m)
return h
# end of the recursive function
n=19
k = list(range(1,n+1))
#Call the recursive function
a = rec(k)
#Convert the only element in the list returned by the recursive function into a string
s = str(a[0])
print("Answer is " + s)
Output:
Problem 2
Print a sequence of numbers starting with a positive number N, recursively, such that A[i+1] = A[i] - 5, as long as A[i]>0. Once A[i] becomes negative, then A[i+1]=A[i] + 5, repeat it until A[i]=N.
Solution:
#Python code
def rec(n):
print(n,end=" " )
if n>0:
n = n - 5
rec(n)
n = n + 5
print(n,end=" ")
# end of recursive function definition
n = int(input("Enter the value of n :"))
rec(n)
Wednesday, August 19, 2020
Kaggle Learn
Learn and practice how to build Machine Learning models for Data Science https://www.kaggle.com/learn/intro-to-machine-learning
Tuesday, August 18, 2020
Web server Vs Application server
Follwing vidoes explans the differences between a web server and application server
- https://www.youtube.com/watch?v=WkaLSZ888as
- https://www.youtube.com/watch?v=ATObcDPLa40
- https://www.youtube.com/watch?v=bgqtxlp7ftc
Monday, August 17, 2020
Saturday, August 15, 2020
Monday, August 10, 2020
How to create an installer for your desktop Java application
You can build an installer (setup file) for your Java app like this creating-an-installer-for-java-desktop-application.
How to build Python executable
Build Python executable from your .py file to run it on Windows without requiring to install Python on your computer py2exe
Saturday, August 8, 2020
Friday, August 7, 2020
Object Serialization in Java
This video illustrates the concept of the 'Serializable Interface' and its use Why to implement Serializable interface
Accessing a Java Bean from a JSP file
This video illustrates how to invoke a JavaBean class from inside a JSP file Accessing a Java Bean from JSP
Thursday, August 6, 2020
Java Bean and EJB
What is a Java bean Java Bean Video
The complete playlist on Advanced Java Advanced Java - Java as a Programming Suite
Monday, August 3, 2020
Saturday, August 1, 2020
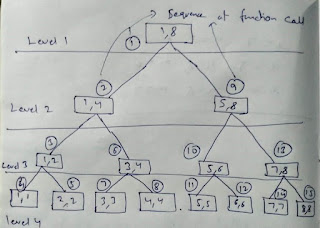
Program Execution (control flow) in a double recursive call
//Understanding double recursion part 1
#include<stdio.h>
//Global variable
int level = 0;
/*
split a list in two equal halves recursively,
and print the level of the binary tree for each node(function call) value pair.
This is the same function used in the DIVIDE & CONQUER technique (splitting
a list from mid recursive ) of Merge Sort.
*/
void split(int low, int high)
{
level++; //increment the level each step downwards journey of program execution
int mid;
//printf("low = %d High = %d Level = %d\n",low,high,level);
printf("%d %d Level = %d\n",low,high,level);
if(low<high)
{
mid = (low + high)/2;
split(low,mid); //split the left half recursively
split(mid + 1,high); //split the right half recursively
}
level--; //decrement level as retrace each step upwards the tree, of program execution.
}
int main(void)
{
printf("For input 1 and 8\n"); // A list of 8 elements, index starting from 1
split(1,8);
printf("For input 1 and 16\n"); // A list of 16 elements, index starting from 1
split(1,16);
return 0;
}
/*
Understanding double recursion part 2
Making both the recursive calls in the
SAME line (return statement) also produces
the same result.
The only difference now is that you need to pass
the level as the third argument to the function.
*/
#include<stdio.h>
//Global variable
int level = 0;
/*
split a list in two equal halves recursively,
and print the level of the binary tree for each node(function call) value pair.
*/
int split(int low, int high, int height)
{
height++; //increment the level each step down
int mid;
printf("%d %d Level = %d\n",low,high,height);
//base condition
if(low == high)
{
return 1;
}
if(low<high)
{
mid = (low + high)/2;
return split(low,mid,height) + split(mid + 1,high,height);// The recursive calls in the SAME line
}
height--; //decrement level as retrace each step upward
}
int main(void)
{
printf("For input 1 and 8\n");
printf("%d \n",split(1,8,level));
printf("For input 1 and 16\n");
printf("%d \n",split(1,16,level));
return 0;
}
Thursday, July 30, 2020
Sunday, July 26, 2020
Thursday, July 23, 2020
Monday, July 20, 2020
How to create charts with Django and Chart.js in a web application.
These videos guides you through building graph web application
- https://www.youtube.com/watch?v=sE08f4iuOhA&list=TLPQMjAwNzIwMjAkmHGlb26-4Q&index=1
- https://www.youtube.com/watch?v=1OL5n06kO_w
How to use Chart.js to build graphs in a web application
- https://www.youtube.com/watch?v=5-ptp9tRApM
- https://www.youtube.com/watch?v=sE08f4iuOhA&list=TLPQMjAwNzIwMjAkmHGlb26-4Q&index=1
These videos explains how to use JavaScript library 'Chart.js' to build charts.
Friday, July 10, 2020
Wednesday, July 1, 2020
Simple Python program to calculate profit percentage
***********File begins here****************
// function definition
//call the function to execute it
findProfit()
***************File ends here**************
Outputs % profit upto 2 decimal points.
Sunday, June 28, 2020
Limits of recursive functions
Thursday, June 18, 2020
A simple Prolog program: facts.pl
Following is how to compile the file
Following is Error because file was not re-compiled after edit
Following is after re-compilation after edit
-
//The HTML index page <!DOCTYPE html> <!-- To change this license header, choose License Headers in Project Properties. To change ...
-
Here are some links to online work sites https://www.upwork.com/ https://www.guru.com/ https://studio.envato.com/freelance-switch/ htt...
-
Acronym Full Form AJAX Asynchronous JavaScript and XML API Application Programming Interface APK Android Application Package ASP Activ...















.png)
