Sunday, June 16, 2019
Netmask
A netmask is a 32-bit binary mask used to divide an IP address into subnets and specify the network's available hosts.
Netmask primarily provides a method to create small subnetworks from a large range of IP addresses. Generally, netmask length is defined in up to 24-bit format for all types of IP classes. The division or creation of networks into subnetworks depends on the class of IP address in use along with their available netmasks. For example, the netmasks for the three IP classes are:
In a netmask, two of the possible addresses, represented as the final byte,
are always pre-assigned and unavailable for custom assignment. For
example, in 255.255.225.0, "0" is the assigned network address. In
255.255.255.255, the final "255" is the assigned broadcast address. These two values cannot be used for IP address assignment.Netmask primarily provides a method to create small subnetworks from a large range of IP addresses. Generally, netmask length is defined in up to 24-bit format for all types of IP classes. The division or creation of networks into subnetworks depends on the class of IP address in use along with their available netmasks. For example, the netmasks for the three IP classes are:
- 255.0.0.0 for Class A with an 8-bit netmask
- 255.255.0.0 for Class B with a 16-bit netmask
- 255.255.255.0 for Class C with a 24-bit netmask
Below is an example of a netmask and an example of its binary conversion.
| Netmask: | 255. | 255. | 255. | 255 |
|---|---|---|---|---|
| Binary: | 11111111 | 11111111 | 11111111 | 11111111 |
| Netmask length | 8 | 16 | 24 | 32 |
A commonly used netmask is a 24-bit netmask, as seen below.
| Netmask: | 255. | 255. | 255. | 0 |
|---|---|---|---|---|
| Binary: | 11111111 | 11111111 | 11111111 | 00000000 |
| Netmask length | 8 | 16 | 24 | -- |
A simple formula can be used to determine the capable amount of networks a netmask can support.
2^(netmask length - # of used segments) - 2For example, if we used a netmask length of 24, having a netmask of 255.255.255.0 with three used segments, subtract three from the netmask length, e.g., 24-3 = 21. With this number determined, plug it into the above formula to get 2^21 - 2 = 2,097,150 total number of networks. You are subtracting two from this number because of the broadcast and network addresses that are already being used.
Another example is a netmask length of 16, having a netmask of 255.255.0.0 with two used segments. Using the above formula, you would get 2^14 - 2 = 16,382 total number of networks.
To determine the number of hosts a netmask is capable of supporting, use the following formula.
2^(# of zeroes) - 2For example, with a netmask length of 24, as shown in the above chart, there are eight zeroes. Therefore, using the formula above, this would be 2^8 - 2 = 254 total number of hosts. Again, two is subtracted from this number to account for the broadcast and network addresses.
Again, another example of a netmask length of 16, there would be 16 zeroes. The formula, in this case, would be 2^16 - 2 = 65,534 total number of hosts.
Below is a breakdown of each of the commonly used network classes.
| Class | Netmask length | # of networks | # of hosts | Netmask | ||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Class A | 8 | 126 | 16,777,214 | 255.0.0.0 | ||||||||||||||||||||||||||||||||||
| Class B | 16 | 16,382 | 65,534 | 255.255.0.0 | ||||||||||||||||||||||||||||||||||
| Class C | 24 | 2,097,150 | 254 | 255.255.255.0 |
Mounting Filesystems in Linux
On Linux and UNIX operating systems you can use the
The
In this tutorial, we will go over the basics of attaching and detaching various file systems using the
For more linuxize.com/post/how-to-mount-and-unmount-file-systems-in-linux
mount
command to attach (mount) file systems and removable devices such as
USB flash drives at a particular mount point in the directory tree.The
umount command detaches (unmounts) the mounted file system from the directory tree.In this tutorial, we will go over the basics of attaching and detaching various file systems using the
mount and umount commands.For more linuxize.com/post/how-to-mount-and-unmount-file-systems-in-linux
Routing Tables
A basic routing table includes the following information:
- Destination: The IP address of the packet's final destination
- Next hop: The IP address to which the packet is forwarded
- Interface: The outgoing network interface the device should use when forwarding the packet to the next hop or final destination
- Metric: Assigns a cost to each available route so that the most cost-effective path can be chosen
- Routes: Includes directly-attached subnets,
indirect subnets that are not attached to the device but can be
accessed through one or more hops, and default routes to use for certain
types of traffic or when information is lacking. Routing tables can
be maintained manually or dynamically. Tables for static network devices
do not change unless a network administrator manually changes them. In
dynamic routing, devices build and maintain their routing tables
automatically by using routing protocols to exchange information about the surrounding network topology.
Dynamic routing tables allow devices to "listen" to the network and
respond to occurrences like device failures and network congestion.
Example: - source: https://searchnetworking.techtarget.com/definition/routing-table
Python: Learn, qualify and work
Links to learn Python. Then qualify tests and get internships/jobs.
Learn sanfoundry.com/1000-python-questions-answers
Qualify and Work: https://rank.sanfoundry.com/python-programming-tests
Learn sanfoundry.com/1000-python-questions-answers
Qualify and Work: https://rank.sanfoundry.com/python-programming-tests
Saturday, June 15, 2019
Friday, June 14, 2019
Monday, June 10, 2019
Sunday, June 9, 2019
AI gurus we all must know
1. Dr. Rina Dechter fellow of the Association for Computing Machinery (the body which gives the Turing Award).
2. Dr. Judea Pearl Got the Turing award in 2011 for inventing the Bayesian Networks.
3. Dr. Geoffrey Hinton Father of modern AI , heGot the Turing award in 2018 .
4. Arthur Samuel Father of Machine Learning.
2. Dr. Judea Pearl Got the Turing award in 2011 for inventing the Bayesian Networks.
3. Dr. Geoffrey Hinton Father of modern AI , heGot the Turing award in 2018 .
4. Arthur Samuel Father of Machine Learning.
Friday, June 7, 2019
System Design of Distributed Systems
Great videos on System design for every software engineer by Gaurav Sen
Thursday, June 6, 2019
UML: Building Blocks
UML great video.
OOSAD: object oriented system analysis and design OOAD
lucidchart.com online UML Tool
OOSAD: object oriented system analysis and design OOAD
lucidchart.com online UML Tool
Monday, June 3, 2019
The Sunk Cost 'fallacy': Financial Management
In economics and business decision-making, a sunk cost (also known as retrospective cost) is a cost that has already been incurred and cannot be recovered.
The sunk cost is distinct from economic loss. For example, when a new car is purchased, it can subsequently be resold; however, it will probably not be resold for the original purchase price. The economic loss is the difference (including transaction costs). The sum originally paid should not affect any rational future decision-making about the car, regardless of the resale value: if the owner can derive more value from selling the car than not selling it, then it should be sold, regardless of the price paid. In this sense, the sunk cost is not a precise quantity, but an economic term for a sum paid, in the past, which is no longer relevant to decisions about the future.
A sunk cost is a cost that has already occurred and cannot be recovered by any means. Sunk costs are independent of any event and should not be considered when making investment or project decisions. Only relevant costs (costs that relates to a specific decision and will change depending on that decision) should be considered when making such decisions.
All sunk costs are considered fixed costs. However, it is important to realize that not all fixed costs are considered sunk costs. Recall that sunk costs cannot be recovered. Take for example equipment (a fixed cost). Equipment can be resold or returned at a determined price, therefore it is not a sunk cost.
Sunk cost is also known as past cost, embedded cost, prior year cost, stranded cost, sunk capital, or retrospective cost.
Assume you spend $200 for a snowboard trip at Grouse Mountain. Later on, you find a better snowboard trip at Cypress Mountain that costs $100 and you purchase that ticket as well. Unknowingly, you find out that the two dates clash and you are unable to refund the tickets. Would you attend the $200 good snowboard trip or the $100 great snowboard trip? A majority of people would choose the more expensive trip because although it may not be more fun, the loss seems greater. The sunk cost fallacy prevents you from realizing what the best choice is and makes you place greater emphasis on the loss of unrecoverable money.
Sources:
1. Wikipedia
2. https://corporatefinanceinstitute.com/resources/knowledge/economics/sunk-cost/
Money already spent and permanently lost. Sunk costs are past opportunity costs that are partially (as salvage, if any) or totally irretrievable and, therefore, should be considered irrelevant to future decision making. This term is from the oil industry where the decision to abandon or operate an oil well is made on the basis of its expected cash flows and not on how much money was spent in drilling it. Also called embedded cost, prior year cost, stranded cost, or sunk capital.
Read more: http://www.businessdictionary.com/definition/sunk-cost.html
The sunk cost is distinct from economic loss. For example, when a new car is purchased, it can subsequently be resold; however, it will probably not be resold for the original purchase price. The economic loss is the difference (including transaction costs). The sum originally paid should not affect any rational future decision-making about the car, regardless of the resale value: if the owner can derive more value from selling the car than not selling it, then it should be sold, regardless of the price paid. In this sense, the sunk cost is not a precise quantity, but an economic term for a sum paid, in the past, which is no longer relevant to decisions about the future.
A sunk cost is a cost that has already occurred and cannot be recovered by any means. Sunk costs are independent of any event and should not be considered when making investment or project decisions. Only relevant costs (costs that relates to a specific decision and will change depending on that decision) should be considered when making such decisions.
All sunk costs are considered fixed costs. However, it is important to realize that not all fixed costs are considered sunk costs. Recall that sunk costs cannot be recovered. Take for example equipment (a fixed cost). Equipment can be resold or returned at a determined price, therefore it is not a sunk cost.
Sunk cost is also known as past cost, embedded cost, prior year cost, stranded cost, sunk capital, or retrospective cost.
Examples of Sunk Costs
- Suppose you buy a ticket to a concert for $150. On the night of the concert, you remember that you have an important assignment due on the same night. You must make a decision: go to the concert or finish your assignment. The $150 paid for the ticket is a sunk cost and should not affect your decision.
- A company spends $5 million building an airplane. Prior to completion, the managers realize that there is no demand for the airplane. The aviation industry has evolved and airlines demand a different type of plane. The company has a choice: finish the plane for another $1 million or build the new in-demand airplane for $4 million. In this scenario, the $5 million already spent on the old plane is a sunk cost. It should not affect the decision and the only relevant cost is the $4 million.
- A company spends $10,000 training its employees to use a new ERP system. The software turns out to be heavily confusing and unreliable. The senior management team wants to discontinue the use of the new ERP system. The $10,000 spent to train employees is a sunk cost and should not be considered in the decision of discontinuing the new ERP system.
- A company spends $10 million to conduct a marketing study to determine the profitability of a new product they will launch in the marketplace. The study concludes that the product will be heavily unsuccessful and unprofitable. Therefore, the $10 million is a sunk cost. The company should not continue with the product launch and the initial marketing study investment should not be considered when making decisions.
The Sunk Cost Fallacy
The sunk cost fallacy reasoning states that further investments or commitments are justified because the resources already invested will be lost otherwise. Therefore, the sunk cost fallacy is a mistake in reasoning in which the sunk costs of an activity are considered when deciding whether to continue with the activity. This is also often known as “throwing good money after bad.”Assume you spend $200 for a snowboard trip at Grouse Mountain. Later on, you find a better snowboard trip at Cypress Mountain that costs $100 and you purchase that ticket as well. Unknowingly, you find out that the two dates clash and you are unable to refund the tickets. Would you attend the $200 good snowboard trip or the $100 great snowboard trip? A majority of people would choose the more expensive trip because although it may not be more fun, the loss seems greater. The sunk cost fallacy prevents you from realizing what the best choice is and makes you place greater emphasis on the loss of unrecoverable money.
Examples of the Sunk Cost Fallacy
In the following examples, you can clearly see how sunk costs affect decision-making. Sunk costs cause people to think irrationally.- Tom purchases a movie ticket online for $12.50 and upon arriving at the theatres to watch the movie, Tom realizes that the movie is really boring and does not appeal to him. Tom decides to sit through the entire movie because he already bought a ticket.
- Jennifer pays a $100 entry fee to join a new tutoring club. After attending 4 of the 7 sessions, Jennifer decides that the tutoring sessions hosted by the club do not help her at all. She decides to attend the remaining 3 sessions despite it being unhelpful because of the $100 entry fee.
Sources:
1. Wikipedia
2. https://corporatefinanceinstitute.com/resources/knowledge/economics/sunk-cost/
Money already spent and permanently lost. Sunk costs are past opportunity costs that are partially (as salvage, if any) or totally irretrievable and, therefore, should be considered irrelevant to future decision making. This term is from the oil industry where the decision to abandon or operate an oil well is made on the basis of its expected cash flows and not on how much money was spent in drilling it. Also called embedded cost, prior year cost, stranded cost, or sunk capital.
Read more: http://www.businessdictionary.com/definition/sunk-cost.html
Sunday, June 2, 2019
Opportunity cost of capital : Financial management
The opportunity cost of capital is the incremental return on investment that a business foregoes when it elects to use funds for an internal project, rather than investing cash in a marketable security. Thus, if the projected return on the internal project is less than the expected rate of return
on a marketable security, one would not invest in the internal project,
assuming that this is the only basis for the decision. The opportunity
coThe opportunity cost of capital is the incremental return on investment that a business foregoes when it elects to use funds for an internal project, rather than investing cash in a marketable security. Thus, if the projected return on the internal project is less than the expected rate of return
on a marketable security, one would not invest in the internal project,
assuming that this is the only basis for the decision. The opportunity
cost of capital is the difference between the returns on the two
projects.st of capital is the difference between the returns on the two
projects.
Source: https://www.accountingtools.com/articles/opportunity-cost-of-capital-definition-and-usage.html
Source: https://www.accountingtools.com/articles/opportunity-cost-of-capital-definition-and-usage.html
Regression Testing (Mutation Testing) : Software Engineering
What is Regression Testing? Definition, Test Cases (Example)
What is Regression Testing?
Regression Testing is defined as a type of software testing to confirm that a recent program or code change has not adversely affected existing features.Regression Testing is nothing but a full or partial selection of already executed test cases which are re-executed to ensure existing functionalities work fine.
This testing is done to make sure that new code changes should not have side effects on the existing functionalities. It ensures that the old code still works once the new code changes are done.
Need of Regression Testing
Regression Testing is required when there is a- Change in requirements and code is modified according to the requirement
- New feature is added to the software
- Defect fixing
- Performance issue fix
How to do Regression Testing
Software maintenance is an activity which includes enhancements, error corrections, optimization and deletion of existing features. These modifications may cause the system to work incorrectly. Therefore, Regression Testing becomes necessary. Regression Testing can be carried out using the following techniques: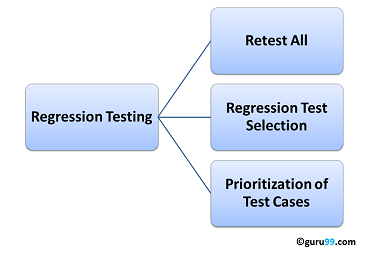
Retest All
- This is one of the methods for Regression Testing in which all the tests in the existing test bucket or suite should be re-executed. This is very expensive as it requires huge time and resources.
Regression Test Selection
- Instead of re-executing the entire test suite, it is better to select part of the test suite to be run
- Test cases selected can be categorized as 1) Reusable Test Cases 2) Obsolete Test Cases.
- Re-usable Test cases can be used in succeeding regression cycles.
- Obsolete Test Cases can't be used in succeeding cycles.
Prioritization of Test Cases
- Prioritize the test cases depending on business impact, critical & frequently used functionalities. Selection of test cases based on priority will greatly reduce the regression test suite.
Selecting test cases for regression testing
It was found from industry data that a good number of the defects reported by customers were due to last minute bug fixes creating side effects and hence selecting the Test Case for regression testing is an art and not that easy. Effective Regression Tests can be done by selecting the following test cases -- Test cases which have frequent defects
- Functionalities which are more visible to the users
- Test cases which verify core features of the product
- Test cases of Functionalities which has undergone more and recent changes
- All Integration Test Cases
- All Complex Test Cases
- Boundary value test cases
- A sample of Successful test cases
- A sample of Failure test cases
Regression Testing Tools
If your software undergoes frequent changes, regression testing costs will escalate.In such cases, Manual execution of test cases increases test execution time as well as costs.
Automation of regression test cases is the smart choice in such cases.
Following are the most important tools used for both functional and regression testing in software engineering.
Selenium: This is an open source tool used for automating web applications. Selenium can be used for browser-based regression testing.
Quick Test Professional (QTP): HP Quick Test Professional is automated software designed to automate functional and regression test cases. It uses VBScript language for automation. It is a Data-driven, Keyword based tool.
Rational Functional Tester (RFT): IBM's rational functional tester is a Java tool used to automate the test cases of software applications. This is primarily used for automating regression test cases and it also integrates with Rational Test Manager.
Regression Testing and Configuration Management
Configuration Management during Regression Testing becomes imperative in Agile Environments where a code is being continuously modified. To ensure effective regression tests, observe the following :- Code being regression tested should be under a configuration management tool
- No changes must be allowed to code, during the regression test phase. Regression test code must be kept immune to developer changes.
- The database used for regression testing must be isolated. No database changes must be allowed
Difference between Re-Testing and Regression Testing:
Retesting means testing the functionality or bug again to ensure the code is fixed. If it is not fixed, Defect needs to be re-opened. If fixed, Defect is closed.Regression testing means testing your software application when it undergoes a code change to ensure that the new code has not affected other parts of the software.
Source: https://www.guru99.com/regression-testing.html
Structural (White Box) testing : Software Engineering
What is Structural Testing ?
Structural testing, also known as glass box testing or white box testing is an approach where the tests are derived from the knowledge of the software's structure or internal implementation.The other names of structural testing includes clear box testing, open box testing, logic driven testing or path driven testing.
Structural Testing Techniques:
- Statement Coverage - This technique is aimed at exercising all programming statements with minimal tests.
- Branch Coverage - This technique is running a series of tests to ensure that all branches are tested at least once.
- Path Coverage - This technique corresponds to testing all possible paths which means that each statement and branch are covered.
Advantages of Structural Testing:
- Forces test developer to reason carefully about implementation
- Reveals errors in "hidden" code
- Spots the Dead Code or other issues with respect to best programming practices.
Disadvantages of Structural Box Testing:
- Expensive as one has to spend both time and money to perform white box testing.
- Every possibility that few lines of code is missed accidentally.
- Indepth knowledge about the programming language is necessary to perform white box testing.
Functional (Black Box) testing: Software Engineering
Functional Testing
Functions (or features) are tested by feeding them input and examining the output. Functional testing ensures that the requirements are properly satisfied by the application. This type of testing is not concerned with how processing occurs, but rather, with the results of processing. It simulates actual system usage but does not make any system structure assumptions.
During functional testing, Black Box Testing technique is used in which the internal logic of the system being tested is not known to the tester.
Functional testing is normally performed during the levels of System Testing and Acceptance Testing.
Typically, functional testing involves the following steps:
- Identify functions that the software is expected to perform.
- Create input data based on the function’s specifications.
- Determine the output based on the function’s specifications.
- Execute the test case.
- Compare the actual and expected outputs.
Source: http://softwaretestingfundamentals.com/functional-testing/
Software Testing: A great video course by NPTEL
Software Testing a very useful course for every software engineer.
Subscribe to:
Comments (Atom)
-
//The HTML index page <!DOCTYPE html> <!-- To change this license header, choose License Headers in Project Properties. To change ...
-
Here are some links to online work sites https://www.upwork.com/ https://www.guru.com/ https://studio.envato.com/freelance-switch/ htt...
-
Acronym Full Form AJAX Asynchronous JavaScript and XML API Application Programming Interface APK Android Application Package ASP Activ...
.png)
